More than a million people are estimated to have been caught out by a Google Docs phishing attack that spread like wildfire this Wednesday –even though Google managed to shut down the vulnerability in less than an hour once it became aware of the scam.
Aside from highlighting just how easily and quickly phishing attacks can propagate across unsuspecting users' email accounts, what makes this worm stand out is that the hackers behind it actually built the scam inside Google's own Docs platform – which played a key role in tricking people into giving their personal information away.
As detailed by Reddit user JakeSteam, who drew attention to the hack, the way the con works is by duping people into thinking they're collaborating with somebody they know on Google Docs – when in fact they're authorising a malicious app to gain access to all of their email and contacts.
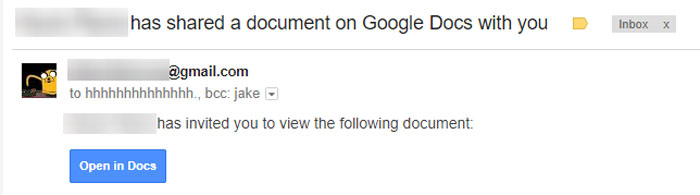
In the attack, users receive an email that looks like a regular Google Docs message, and which appears to have been sent from somebody they know.
The email contains an invitation to view a document, and when people click on the link to open the doc, they're taken to an authentic Google Docs web page – but here's where things get really sneaky.
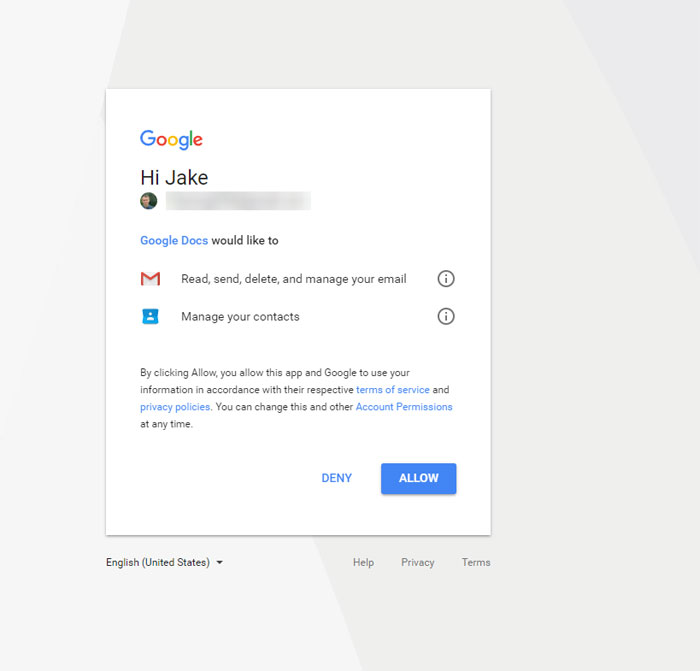
On this permissions page (which, again, is a real Google page), users are asked whether they're willing to authorise 'Google Docs' to access their email and contacts – but the trick here is that this 'Google Docs' isn't the web platform itself, but a malicious app that has simply been named "Google Docs".
 JakeSteam/Reddit
JakeSteam/Reddit
It could have been called "Jane" or "Team Spreadsheet" or "Malicious Link". But by calling it "Google Docs", the hackers were relying on people being blasé about clicking on what looks to be just another innocuous Google app message – and that reliance appears to have been well-founded, given an estimated million or more people proceeded to authorise the impostor.
In doing so, they were actually granting the hackers the ability to read, send, and delete their email, and to manage their contacts.
What's more, the attack automatically propagated itself once people had authorised the app, spamming everybody in affected users' contacts list with the fraudulent Google Docs email invitation. Fortunately, Google acted pretty quickly on Wednesday to shut the scam down.
"We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts," the company said in an official statement.
"We've removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again. We encourage users to report phishing emails in Gmail."
 JakeSteam/Reddit
JakeSteam/Reddit
Despite the extent of the permissions that affected users unwittingly granted to those behind the attack, Google later clarified that its investigations showed that only contact information was exposed while the phishing campaign was live – which presumably means the actual content of emails wasn't accessed.
"There's no further action users need to take regarding this event," the company says.
"[U]sers who want to review third party apps connected to their account can visit Google Security Checkup."
But while Google Security Checkup allows people to verify devices connected to their Google account and check which apps and websites have been granted access to their account, commentators have criticised Google for enabling third-party apps in its own systems to be able to impersonate the company so easily.
Massive oversight in allowing non-Google apps to call themselves Google, in Google's own web interface. Incredible. https://t.co/lZP3eGdnIy
— SwiftOnSecurity (@SwiftOnSecurity) May 3, 2017
According to Google, the company has ways of preventing this kind of abuse of its OAuth system – which enables logged-in users to authorise access to apps and websites without manually re-entering their login credentials.
In this case those strategies clearly didn't work, as the hackers were able to effectively masquerade themselves as one of the world's biggest tech companies, simply by calling their app "Google Docs" – even though the company was warned years ago that attackers might try to compromise users' accounts by posing like this.
But despite the cunning simplicity of the attack's presentation – which would have made it difficult for many to discern that something was fishy – experts say there were tell-tale signs indicating that something wasn't right.
"In this case, the OAuth message did correctly state that the application asked for access to the user's email," researcher Johannes Ullrich from security firm the SANS Institute told Threatpost.
"This 'should' have been a tip off that the application wanted to do more than share a document."
Ultimately, this attack serves as a timely reminder to all of us to be on the lookout for anything unusual in the emails we receive – particularly when they're emails we weren't expecting to see, inviting us to collaborate on documents we don't know anything about.
Of course, when those emails look just like every other regular Google Docs email, the fakes might be pretty hard to spot – but we all need to be careful, especially since experts say the publicity and success of this hack could now lead to other similar phishing campaigns.
"Now that this technique is widely known, it's likely to pose a significant problem," the CEO of security company Jask, Greg Martin, told Alfred Ng at CNET.
"[T]here are so many online services which use OAuth and it's difficult for them to fully vet all of the third-party applications out there."
