Security researchers have announced the discovery of an advanced malware platform that has operated undetected for at least five years.
According to experts, "ProjectSauron" is so advanced and well designed that it's likely the work of a state-sponsored hacking group – ie. backed by a government intelligence organisation.
The malware has been active since at least 2011, targeting high-profile networks in Russia, China, Sweden, and other countries.
Researchers at computer security firms Symantec and Kaspersky Lab detected the malware in a joint effort, and say it's been discovered in more than 30 infected sites so far – including an airline in China, an embassy in Belgium, and an unidentified organisation in Sweden.
Unlike the kind of consumer-targeting malware that affects regular PCs, ProjectSauron – which also goes by the name Remsec – has a more specific focus, although it does run on common Microsoft Windows platforms.
The malware is designed to infiltrate computer networks run by organisations such as governments, military sites, scientific research centres, and corporate IT systems.
It aims to spy on infected networks, opening a back door to compromised systems, logging keystrokes, and stealing personal information, like user credentials and passwords.
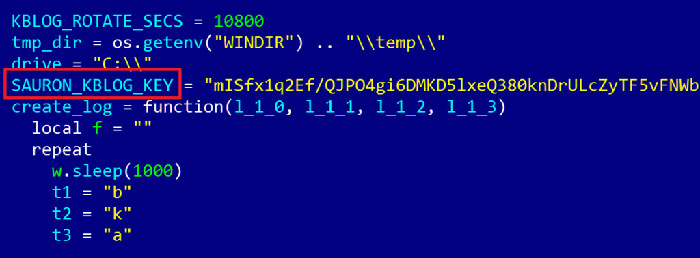 Kaspersky Lab
Kaspersky Lab
The ProjectSauron name comes from references to "Sauron" in the malware's code (see the image above), and Symantec says it's been created by a previously unknown hacking group called Strider – who are clearly fond of their The Lord of the Rings references.
One of the reasons it took so long for security experts to detect ProjectSauron is that the program is designed to be almost invisible, with the attackers using unique code for each separate target. This means the malware doesn't trigger the red flags computer scientists usually look for in malicious code.
Despite being active since 2011, Kaspersky Lab only discovered the hackers' work last year, when the company was asked by one of its clients to look into some anomalous network traffic.
"The attackers clearly understand that we as researchers are always looking for patterns," researchers from Kaspersky Lab explain. "Remove the patterns and the operation will be harder to discover."
Symantec describes ProjectSauron as having a number of "stealth features", including storing its components in executable objects that make it harder for traditional antivirus software to properly detect. It's also capable of infecting 'air-gapped' computers that aren't connected to the internet, through the use of USB keys.
"[M]uch of the malware's functionality is deployed over the network, meaning it resides only in a computer's memory and is never stored on disk," the researchers write in a blog post. "This also makes the malware more difficult to detect and indicates that the Strider group are technically competent attackers."
The good news is that Kaspersky says ProjectSauron activity appears to have largely ceased this year in terms of the infected sites the company's researchers are aware of – but there's no guarantee things will stay that way.
After all, the teams think that such a sophisticated malware platform had to have government backing from somewhere – which means a lot of planning and money went into this attack, and it's probably not over yet.
"We think an operation of such complexity, aimed at stealing confidential and secret information, can only be executed with support from a nation-state," Kaspersky Lab explains. "ProjectSauron is likely to have required several specialist teams and a budget probably running into millions of dollars… We are aware of more than 30 organisations attacked, but we are sure that this is just a tiny tip of the iceberg."
