An unprecedented ransomware attack spread across the globe on Friday and into the weekend, amounting to what may be the largest online extortion scam the internet has ever seen.
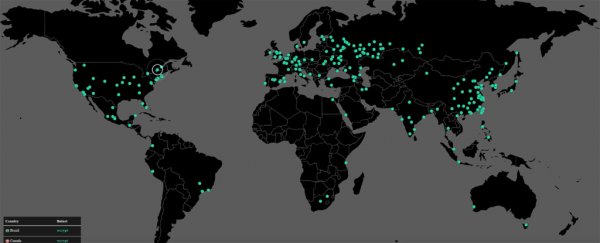
So far, the 'WannaCry' ransomware worm has infected an estimated 230,000 computers in 150 countries, causing chaos and shutting down hospital systems, transport networks, manufacturing plants, and universities.
While security researchers have acted quickly to halt the attack, experts fear the beginning of the work week could see thousands of new systems compromised as employees log on to vulnerable PCs.
The WannaCry malware – which also goes by other variant names, including WannaCrypt and Wanna Decryptor – was unleashed on Friday, striking vulnerabilities in unpatched Windows systems in thousands of organisations across the world.
The worm is a form of ransomware, where affected users are asked to pay a ransom fee in order to regain control of their systems. In the case of WannaCry, the malware locks their system, presenting a pop-up window that tells users their files are encrypted and will be deleted unless they choose to cough up US$300 to be paid in Bitcoin.
Ransomware isn't new, but the extremely quick and pervasive spread of WannaCry is thought to be unprecedented, hitting everything from the UK National Health Service to FedEx, Spanish telco Telefónica, and the Russian Interior Ministry among many others.
Security researchers are still scrambling to learn more about how the malware operates, but it's understood that WannaCry exploits a vulnerability in older, outdated Windows systems including Windows XP, Windows 8, and Windows Server 2003.
That vulnerability was patched for supported Windows systems back in March, but after WannaCry pretty much exploded on Friday, Microsoft took the unusual step of issuing patches for these vulnerable older operating systems – which you can access here.
At least, that's the vanilla version of the WannaCry weak spot – but the actual back story on this vulnerability is heck of a lot murkier.
The malware actually makes use of a covert security exploit reportedly developed by the US National Security Agency (NSA) to infiltrate Windows computers.
This exploit, called EternalBlue, was leaked by a hacker group called the Shadow Brokers in April – but even though Microsoft had already patched the vulnerability in March, the chaos caused by WannaCry shows that hundreds of thousands of computers weren't running the patched software, or were running older OSs like Windows XP that were never eligible to receive the patch until last Friday.
The good news – in addition to Microsoft's prompt patching for older OSs – is that shortly after WannaCry started making trouble on Friday, a security researcher in the UK known by the moniker MalwareTech stumbled upon a crucial piece of data in the malware's code.
Once a PC is infected by the malware, the worm spreads by checking for other systems on the local network that may be infected through the unpatched vulnerability. It also attempts to make connections with random IP addresses on the internet in search of further vulnerable systems.
Discovering a domain name hidden in WannaCry's programming – perhaps a failsafe URL embedded by the perpetrators so that they could control their creation – MalwareTech suspected it could be used to circumvent the worm.
By subsequently registering the domain name – creating what's called a "sinkhole" to prevent the malware spreading – the researcher was able to fool the code into thinking it was being run inside a virtual environment, in which case the malware exits the system.
It's unknown how many thousands (or hundreds of thousands) of PCs this clever ruse ultimately ended up saving from WannaCry's clutches – but the hard truth is that other strains of the malware have since been detected by other security researchers, and these newer versions can't be fooled by the same trick.
What that means is that it's essential for Windows users to make sure they're running an updated, patched build of their OS that can't be infected by WannaCry or its newer strains.
In addition, it's important to run antivirus or other security software, and keep a separate backup of all your important data, so that if your PC does get hijacked by ransomware, your personal files aren't at risk.
Despite the brazenness of this extortion scam – which has now sparked law enforcement to mount an international manhunt to catch the unknown perpetrators behind WannaCry – it seems the crooks haven't exactly made it rich with the stunt, netting just over US$26,000 on the first day of the attack.
Of course, those numbers could change this week if people aren't careful about updating and patching their Windows PCs, but in any case, experts say the last thing you should do is pay these scammers if they infect your computer, because that's only encouraging this illegal activity.
"Cyber attacks have already become a kind of industry," cyber security researcher Yang Xiang from Deakin University in Australia told ABC News.
"I don't think it's ethical to pay ransom to get data back because we really need to have strong mechanisms to defend against attackers… If you keep paying ransom it's actually helping attackers to grow the industry."